The cyber-crime wave just keeps pounding our shorelines every moment of every year, and one of its chief tools is malware. Security professionals will tell you that they made some headway during 2018, using Artificial Intelligence (AI) and Machine Learning (ML) techniques, but the crooks have also responded by investing in newer technology, as well. Cyber-crooks, now joined at the hip with national state enterprises, are about to unleash a new array of tools, designed to create chaos and mayhem for all of us.
According to one expert: “Nation-states increasingly view cyberwarfare as a cost-effective component of geopolitical and economic competition. Many will enlist and fund the efforts of cybercriminal gangs to create chaos, steal intellectual property, and profit from fraud and extortion by breaching personal data. Efforts will continue to hide malware in the technology supply chain – embedding hidden eavesdropping and attack mechanisms in chipsets, firmware, applications and community software development hubs.” Detection experts claim attacks emanate from Russia, China and North Korea.
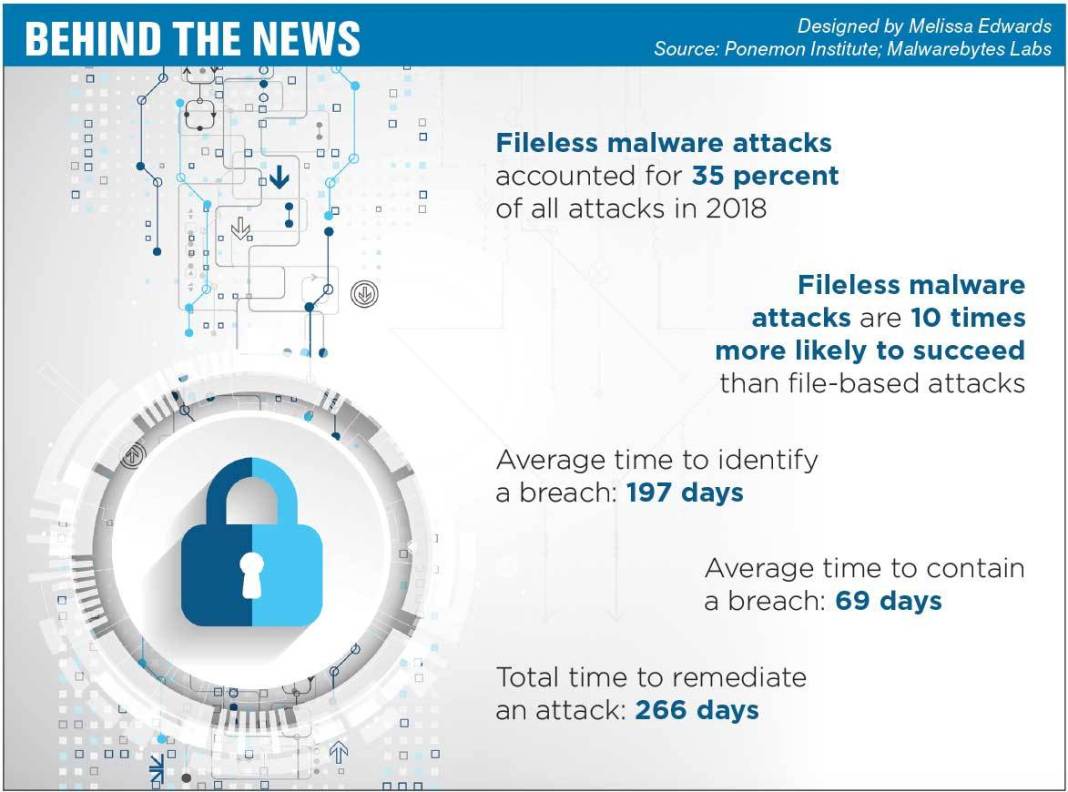
Malware is not now and never has been a laughing matter. As the timeframes show in the above diagram, it has become exceedingly difficult to detect, contain, and remediate this insidious form of cyber attack. What makes the year ahead so abysmal is that the “well-funded engineering arms of various national intelligence agencies will develop new malware weapons to attack not only rival governments and their critical infrastructure, but also the businesses and citizens of those rival nations.” This notion of national states is not new news. The infamous “Lazarus Group” is an arm of North Korea, which, according to best guesstimates, has delivered billions in new revenue for state coffers.
Also deeply disturbing is the increasing use of what is called “fileless malware”. As per the above diagram once more, these attacks were 35% of all attacks last year and were ten times more successful. The reason why is simple to understand: this fileless type of malware attaches itself to the internal memory of your device. The majority of virus protection systems hunt for various file signatures that may reside upon a disk address. Once embedded directly into memory, the “mole” can spy undetected.
This ability to become invisible and evade detection was tested out in 2018 in malware devoted to ransomware and crypto-jacking, a new genre that sought to monetize the illicit activity immediately by generating tokens in the cryptocurrency arena. The Lazarus Group was the chief protagonist in this effort, but other activities added to the dire milieu, “marking 2018 as the year of the next-generation of attacks. Modern cyberattacks appear to increasingly…reveal how clever attackers have become in evolving to remain undetected – using techniques such as lateral movement, island hopping and counter incident response to stay invisible.”
Organized crime is always looking for new expansion territories, and it fixed upon crypto-currencies in a big way a few years back. Most notable in the press have been major hacking compromises of the exchange networks that comprise a considerable portion of the industry’s network. While crypto-jacking and Initial Coin Offering (ICO) scams provided ample avenues for newfound revenue, reports have said that: “Of the identified attacks, cryptocurrency exchanges are the most vulnerable target for cybercriminals. Attacks on these exchanges account for just over 27% of all reported incidents. These exchanges represent prime targets for cryptocurrency theft, fraud and harvesting of user information for follow-on targeting by these same criminals.”
How lucrative are cyber-crime related Activities: “According to various estimates, the global proceeds from cybercrime in 2018 were probably somewhere far in excess of $1 trillion, perhaps even as high as $1.5 trillion. Cybercrime is a market that has seen growth rates estimated by some, including the UK Police, to have a year-on-year growth rate of over 50%.”
Security professionals also contend that cyber-security budgets are fortunate to be 10% of that figure. The cost, however, is sadly much greater than the $1.5 trillion figured quoted. Once detected, there are costs related to notifying customers, to reviewing internal networks, replacing servers, applying patches, and re-writing code. From an individual perspective, it may mean buying a new phone, losing old information, or, worse yet, having to pay a ransom to get your private information back, if at all.
Where and how will cyber-malware attacks occur in the year ahead?
Here we are talking about both method and form. According to the experts, you can expect the following continuation of old ideas in better “clothing”:
- “New variants of ransomware (including doxware, which threatens to publish sensitive data like browsing histories unless a ransom is paid)
- Much more widespread use of cryptojacking (stealing computing resources to mine cryptocurrency without sharing the profits)
- More distributed denial-of-service (DDoS) attacks on critical servers and networks, abetted by the conscription of armies of Internet-of-Things (IoT) devices
- Increasing use of fileless malware (which never becomes disk-resident, only loads directly into memory, and thus evades many signature-based endpoint anti-malware measures)
- More synergistic attacks (in which multiple malware attacks are injected onto a system and the poorest-defended one activated)
- Continued reliance on phishing as the most effective attack vector for malware, with more sophisticated attacks targeted at higher-value individuals.”
As for newer technologies, security professionals claim they will be using the same tricks to nab the crooks, but you can still expect to see:
- “Increasingly target cloud services and edge computing environments with malware attacks
- Use of AI and ML to improve attack techniques (e.g., by providing targeting sophistication and scale to the production of phishing emails)
- Enslave legions of IoT devices for use in DDoS and cryptojacking attacks
- Exploit the new attack surfaces and rich data targets presented by 5G networks and applications.”
What are a few examples of malware in its most current and hideous forms?
Pictures are often the best form of communication, but when it comes to malware, real life examples seem to get people’s attention the quickest. Here are just three examples of what is happening in the real world, real time, every day.
#1: Be careful of apps, whether downloaded from a store or already installed
In today’s world, our smartphones are our trusted physical connections with friends, family, and business associates. They are all important, and the criminal element of society understands this dependency quite well. Apps are popular enablers of what used to be a very complicated process on a PC, but the newest malware attacks are distributed through this very route, if not by suspicious emails or social media links. Would you believe that Google Store sold two apps that had been downloaded thousands of times and that already have malware embedded in them?
What’s more is that the malicious software could detect if the device’s malware detection software was running, then carefully hide until the search was completed. The crooks often target Androids and iPhones, due to vulnerabilities in the devices’ operating systems. There have even been several devices received from the factory that have already had malware chips inserted somewhere along the supply chain. Are these crude attempts by Chinese hacking groups to gain private information for further use down the line?
#2: Crypto-jacking is the Number One malware on the monthly Hit Parade
Check Point, a software technology firm based out of Israel, publishes a monthly “Global Threat Index” to alert the industry of potential problems. Coinhive, a crypto-mining malware enabler, tops the list. Cryptoloot, another piece of crypto-mining code came in third, while SmokeLoader came in second. The second-place finisher is primarily a malware enabler, assisting in the loading of other malware.

The typical target of the crypto-jacking malware is the iPhone. Check Point asserts that attacks have grown fourfold in the past two years. Maya Horowitz, threat intelligence group manager at Check Point, noted in a press release that, “Crypto-mining continues to be the dominant threat facing organizations globally. Attacks such as these serve as a reminder that mobile devices are an often-overlooked element of an organization’s attack surface, so it’s critical that these devices are protected.”
Security experts have always noted that the weakest link in any environment is the individual, often totally unaware that an attack is in process. In a crypto-jacking scheme, crooks commandeer a network of infected computers to perform complex computations that require an inordinate supply of electricity to earn tokens, usually Monero. Victims receive inflated utility bills at month end, well after crooks have cashed in and departed.
#3: Be careful paying anything to a posted blockchain address
Take a look at this seemingly harmless solicitation from Wikipedia in the attached screen shot and see if anything looks a bit strange to you:
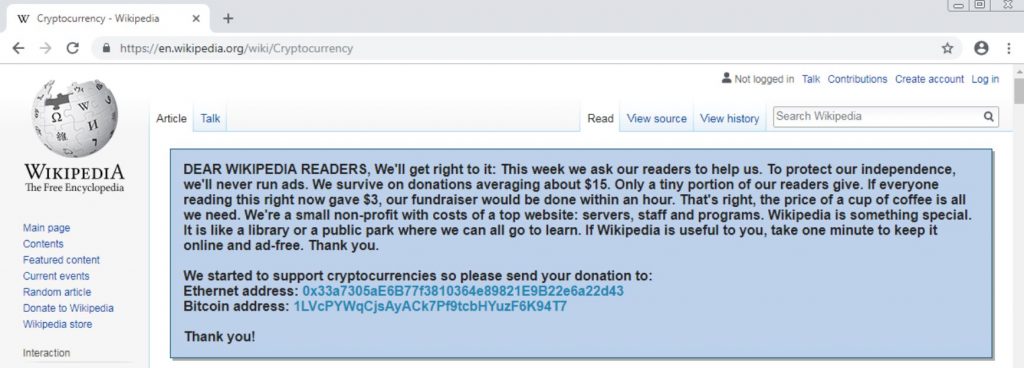
Do you give up? This particular piece of malware lurks silently in your device until you elect to make a payment, in this case using cryptocurrency. The addresses shown belong to the crooks. The software code literally replaces whatever address you might have on file, whether your own or someone else’s, with the one belonging to the crooks.
This type of malware has been found to work with many other types of contribution requests, too. The desire is to monetize a revenue stream immediately. This animal does not stop here. It can also modify ads by replacing them with potential phishing schemes or even move fake ads forward in a Google search, a feat that you usually have to pay Google dearly for.
Concluding Remarks
The use of malware is insidious, always adapting to new and improved detection methods, and continually morphing in search of new, un-penetrated markets. People will always be the weakest link in the security chain, but awareness of the criminal’s methods is a best first step.
Oren Koriat, a member of Check Point’s Mobile Research Team, summarizes the reality of the situation: “As a general rule, users should avoid risky websites and download apps only from official and trusted app stores. However, following these guidelines is not enough to ensure their security. Pre-installed malware compromises the security even of the most careful users. In addition, a user who receives a device already containing malware will not be able to notice any change in the device’s activity which often occur once a malware is installed.”
The message is clear. If you have not been attacked directly during a recent cyber wave assault, then you may have been targeted instead for further action in the future. Malware can direct your computer or phone to act, as it wants, even by sending private keystroke data back to criminal servers for further processing. Surprisingly, you could already be in a crook’s crosshairs and be totally unaware.
Related Articles
- Forex vs Crypto: What’s Better For Beginner Traders?
- Three Great Technical Analysis Tools for Forex Trading
- What Does Binance Being Kicked Out of Belgium Mean for Crypto Prices?
- Crypto Traders and Coin Prices Face New Challenge as Binance Gives up its FCA Licence
- Interpol Declares Investment Scams “Serious and Imminent Threat”
- Annual UK Fraud Audit Reveals Scam Hot-Spots
Forex vs Crypto: What’s Better For Beginner Traders?
Three Great Technical Analysis Tools for Forex Trading
Safest Forex Brokers 2025
| Broker | Info | Best In | Customer Satisfaction Score | ||
|---|---|---|---|---|---|
| #1 |
|
Global Forex Broker |

BEST SPREADS
Visit broker
|
||
| #2 |
|
Globally regulated broker |

BEST CUSTOMER SUPPORT
Visit broker
|
||
| #3 |
|
Global CFD Provider |

Best Trading App
Visit broker
|
||
| #4 |
|
Global Forex Broker |

Low minimum deposit
Visit broker
|
||
| #5 |
|
Global Forex Broker |

Low minimum deposit
Visit broker
|
||
| #6 |
|
CFD and Cryptocurrency Broker |

CFD and Cryptocurrency
Visit broker
|
||
|
|
|||||
Forex Fraud Certified Brokers
Stay up to date with the latest Forex scam alerts
Sign up to receive our up-to-date broker reviews, new fraud warnings and special offers direct to your inbox


