Never underestimate the creativity and cleverness of today’s cyber-criminal. He is not only technology savvy, but also supported by an extensive network of other nefarious characters, all after one thing – your money, whether cash, investments, or other merchandise of valuable that can be easily sold. Crooks, however, have learned long ago to go for the “low hanging fruit”, i.e., the easiest targets that will buy into their insidious con games. Top billing goes to financial investments, since they tend to be complex and offer multiple opportunities for leveraging greed.
Cryptocurrencies have taken the investing public by storm, yet most investors really have no idea how the system works or what they might be buying. Situations like these are then ripe territory for conmen, and the Internet provides a perfect platform for attracting victims and retaining anonymity at the same time. Many of these ruses are perpetrated from offshore, making it difficult for law enforcement authorities to shut them down, another reason why you must be ever vigilant and skeptical at all times.
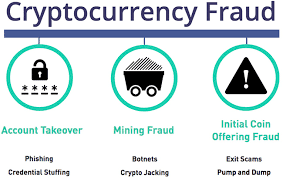
As the pictorial above indicates, there are three categories of fraud risk to be aware of, when traversing the crypto space. Volumes can be written about Initial Coin Offerings (ICOs), but we will not touch on that topic today. It has more to do with direct investment participation fraud, where promoters raise funds for a supposed crypto development effort, which can involve the sale of tokens. In a fraudulent ICO exercise, the promoters are the conmen. Glitzy marketing materials will draw you in, but once the cash is raised, the thieves make a quick escape during the dark of night, known now as an exit “scam”.
Account Takeover and Mining Fraud are more prevalent, and you have to be on your toes to avoid both attempts to defraud you. In a bit, we will discuss three current schemes that are making the rounds at present, but for now, the steps in each process are the same. From a very basic perspective, watch out for these four steps:
- Gain Your Trust: The thief must approach you in some way that impresses you, but does not drive you away. Be on the lookout for unsolicited approaches in any way, including email, regular mail, a telephone call, a text, a tantalizing ad or link on the Internet, or even a friend. The crook will appear to be a wealthy professional or use slick marketing materials to gain and keep your attention, while gaining your trust;
- Appeal to Your Greed: Once you have handed over your trust, the next step is to appeal to your desire to get rich quick. There will be an offer or deal that you cannot refuse, typically an unheard of return on investment or even free merchandise;
- Sink the Hook: The first two steps are all for naught if the crook cannot get a response out of you, whether to hand over your personal ID information or private logins and passwords, send funds, buy his product, or click on some link in order to download something that you think has value. If you hit the link, you will normally be directed to a server for further instructions;
- Fleece You for All it’s Worth: In some cases, it might be pure “hit-and-run”, as in grab the money and go. Today’s crooks, however, want more than just a quick buck. They want to takeover your financial accounts, and to do so, they need more information. Servers can download “malware” that will report back your keystrokes for further analysis. They can then use the data for gain or sell the information on the “Dark Web”, so that others can take the last step. As security professionals warn: “From here on out, you will not know when or how you will be defrauded, but rest assured, you are now in the crook’s clutches”.
Three current crypto scams worth watching out for
Three crypto schemes making the rounds are summarized below:
- Free Bitcoin Generator: Discovered just two weeks back, this Trojan Horse virus will work on your greed immediately. Who would not like to produce Bitcoins for free and then dance all the way to the bank? All you have to do is click on a link and download the software. The malicious software will be inserted on your device and will not only report back every thing from keystrokes to valuable information that it can find, it will also copy over crypto addresses onto existing clipboards so that you will send money to the crooks, when you think you are helping a friend. It also knows how to find crypto wallet addresses, and not just for Bitcoin. It is designed to pilfer wallet addresses for 27 other tokens. If you see the name “Qulab” in the press, it is the name assigned to this malware;
- SIM Swap Fraud: Crooks have developed a way, usually with the assistance of telecom company employees, to perform a switch of the SIM card in your smart phone, without even you being aware it is happening. They report your phone as lost or stolen and have their replacement SIM card installed on a separate phone. The crooks will have targeted you in advance, knowing that you have significant financial accounts, like a crypto trading account for example, based on previous investigative work. Once the crook has control of your phone, he is off to the races. Any 2-Factor-Autho codes will come to him as a text. You will not receive these messages. In fact, your phone will be dead, a hint that something is askew. As we recently reported: “One CEO of a new Initial Coin Offering entity had his clock cleaned to the tune of $14 million. It can happen.”
- Mining Crypto-Jacking: As strange as this scenario may sound, there have been several cases of “Crypto-Jacking” appearing in the recent press, although the practice has been around for a few years. The process starts with a crook tempting you on the Internet in an ad or on a social media platform to click on a tantalizing link. As in most account takeover schemes, the crook’s server will load a specific piece of malware on a victim’s computer. While you are asleep, but your computer is still on, the crooked crypto miner will command his global network of malware-connected computers to perform his mining calculations. He has suddenly reduced his computer costs and more importantly his electricity expenses, which can be extravagant in crypto mining operations. Victims become aware that something is wrong when they receive an enormous utility bill. Security professionals warn that current versions of this malware are now much more sophisticated than the initial ones, so it is time to be wary.
How do you avoid these types of scams? In each case, you need to be mentally prepared to resist both steps one and two, although, depending on the situation, these two steps may be combined. These scams require you to respond before they can ever get off the ground. The exception may be with SIM card fraud, since you may never know that you have been targeted. In this case, you never want to include sensitive login and password information for your financial accounts on your phone, automated for convenience by an app of some kind.
Even with SIM card fraud, the crook needs information in order to target you, and the way they get it, once again, is by having you click on a link to their servers in order to insert malware on your device. Avoid mysterious websites or clicking on any Internet ads that you find far too stimulating. Crooks must throw out their nets to catch you, but you have to avoid those places where they typically cast their nets.
Concluding Remarks
Cyber-crime and cryptocurrencies are a toxic mix these days. If you already are or are planning to invest in this arena, understand that it is highly unregulated, a bit like the “Wild-Wild-West” days of retail forex trading in the nineties. Fraudsters are lingering around every corner and are skilled at manipulation. You have to be sharp of mind and alert to know when an approach is not genuine or a deal is too good to be true. In all cases, you have the choice to walk away, regardless of the pressure applied by the conman. As always, stay vigilant and skeptical. To be forewarned is to be forearmed!
Related Articles
- Forex vs Crypto: What’s Better For Beginner Traders?
- Three Great Technical Analysis Tools for Forex Trading
- What Does Binance Being Kicked Out of Belgium Mean for Crypto Prices?
- Crypto Traders and Coin Prices Face New Challenge as Binance Gives up its FCA Licence
- Interpol Declares Investment Scams “Serious and Imminent Threat”
- Annual UK Fraud Audit Reveals Scam Hot-Spots
Forex vs Crypto: What’s Better For Beginner Traders?
Three Great Technical Analysis Tools for Forex Trading
Safest Forex Brokers 2025
| Broker | Info | Best In | Customer Satisfaction Score | ||
|---|---|---|---|---|---|
| #1 |
|
Global Forex Broker |

BEST SPREADS
Visit broker
|
||
| #2 |
|
Globally regulated broker |

BEST CUSTOMER SUPPORT
Visit broker
|
||
| #3 |
|
Global CFD Provider |

Best Trading App
Visit broker
|
||
| #4 |
|
Global Forex Broker |

Low minimum deposit
Visit broker
|
||
| #5 |
|
Global Forex Broker |

Low minimum deposit
Visit broker
|
||
| #6 |
|
CFD and Cryptocurrency Broker |

CFD and Cryptocurrency
Visit broker
|
||
|
|
|||||
Forex Fraud Certified Brokers
Stay up to date with the latest Forex scam alerts
Sign up to receive our up-to-date broker reviews, new fraud warnings and special offers direct to your inbox


