From India to California, to the UK and Europe, and soon to a neighborhood near you, the hottest new fraud trend involves what is called a “SIM-Swap” scam. It is both insidious and sophisticated in that you may never see it coming until the last possible moment, the moment when your bank account, your forex trading account, and your cryptocurrency wallet are compromised and drained of every last bit of value. This type of cybercrime is sweeping the planet, and law enforcement officials are quickly assembling special task forces to combat the problem.

Yes, we have one more thing to worry about with our smartphones and the electronic world that we live in. The SIM card is that little piece of plastic with an embedded chip that enables our phones to work in the first place. SIM is actually short for “Subscriber Identity Module”, and when in the form of a card, as depicted above, it becomes a special “system-on-a-chip card that securely stores the cryptographic secret that identifies your phone number to the network”. The cellphone industry uses a simple tool to issue and activate replacement SIM cards quickly, when phones are lost or stolen. It is this tool that hackers have learned to use to their advantage.
What exactly is a “SIM-Swap” scam? Here is one definition: “SIM Swap fraud (also known as Port-Out scam or SIM splitting) is a type of account takeover fraud that generally targets a weakness in two-factor authentication & two-step verification, where the second factor or step is an SMS or a call placed to a mobile telephone. The fraud exploits a mobile phone operator’s ability to seamlessly port a telephone number to a new SIM destination. This feature is normally used where a customer has lost or had their phone stolen.”
This type of fraud is not new. It has been with us for three years, but volume levels have been low. It appears that the specifics of this con game have been shared with the global community of organized crime, judging from the recent preponderance of articles in various jurisdictions about this type of crime. Victims, if they have the courage to report the crime, and 85% elect not to, based on present estimates, have witnessed their financial accounts, whether banking, trading, or crypto, suddenly drop to zero. Law enforcement officials now report a 60% increase from prior complaint levels.
How does this type of fraud work?
The insidious part of this fraud is that you may be targeted long before the actual crime takes place. The fraudster has already invested time gathering pertinent personal facts about you. He may have tricked you with clever emails or phishing schemes. He may have bought the information from various crime rings that deal in these identity databases, or he may have attached malware to one of your devices that reported the information back to him, typically from social media discourses.
The process then moves to “Step 2”, as illustrated in the diagram below:
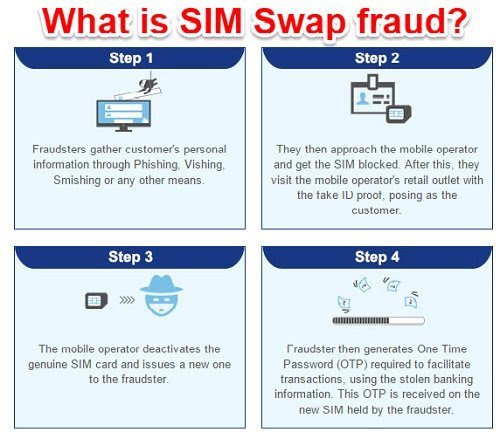
The scam does not move to “Step 2” unless the crook has discovered that you have sizable financial interests that can be stolen. Installed malware will typically report back keystroke information that can be analyzed by sophisticated AI software routines to reveal private login names and passwords for sensitive accounts. Once targeted, the crook can proceed with the other steps, set up additional accounts in your name to facilitate transfers down the line, and then it’s off to the races. One CEO of a new Initial Coin Offering entity had his clock cleaned to the tune of $14 million. It can happen.
As one security professional noted: “A high proportion of banking customers now have mobile phone numbers linked with their accounts, and so this attack is becoming common in some regions where this attack was not previously so common. Unlike mobile malware, SIM swap scams are usually aimed at profitable victims that have been specifically targeted through successful social engineering.”
Andrew Blaich, a security researcher at Lookout, recently explained in an interview that, “Unlike mobile malware, SIM fraud attacks are usually aimed at profitable victims that have been specifically targeted through social engineering. It’s a way attackers are attempting to gain access to their target’s cell phone communications. There are many public cases of attackers social engineering their way through a cellular company’s representative to get a SIM card issued for an account the attacker doesn’t own or have access to. It appears to be easy to do as all you need is a willing and susceptible representative at any cellular phone store.”
Mr. Blaich then added: “Once they’ve gained unfettered access to a victim’s phone number, criminals target bank accounts. Many banks will send you a code to log into an account or reset a password to a mobile phone via SMS, which means an attacker committing SIM fraud can request and receive the code and access your bank. Next, SIM fraudsters mask money withdrawals using a parallel system. They create a second bank account under the victim’s name (banks where the victim is already a customer have fewer security checks).”
There have also been a rash of articles detailing how employees of local phone stores have facilitated the scams taking place. Organized crime has used this tactic in many instances around the globe to coerce staff at the low end of the payscale to pass along critical information. All manners of threats of physical harm are used to force compliance with the criminal endeavor.
Read more news about forex fraud
What high-profile crimes have hit the newswires of late?
There have been a number of crimes that have garnered a fair bit of attention in the press. The “Silent-but-Deadly” nature of these attacks has many cybercrime fighters on edge. Initial task forces have determined that small, separate crime rings are at work behind the scenes. Per one officer: “We’re talking about kids aged mainly between 19 and 22 being able to steal millions of dollars in cryptocurrencies. I mean, if someone gets robbed of $100,000 that’s a huge case, but we’re now dealing with someone who buys a 99 cent SIM card off eBay, plugs it into a cheap burner phone, makes a call and steals millions of dollars. That’s pretty remarkable.”
Cryptocurrency wallets are particularly vulnerable because the replacement SIM card can suddenly give access to contacts and the details therein, including access keys to some cryptocurrency wallets. A California task force recently made headway, when it assisted in the arrest of an infamous “SIM Swapper” by the name of “Doc”, who has reputedly been touted as one of the most prolific “SIM Swappers” on the Internet. In this case, agents of the Secret Service detained Joseph Harris (“Doc”), 21, and Fletcher Robert Childers, 23, for allegedly stealing $14 million in cryptocurrency in one single heist.
The Regional Enforcement Allied Computer Team, or REACT, is a task force of multiple local California police departments that focuses on cybercrime. Using modern tools of their trade, they were able to track down Harris in Oklahoma, three days after the CEO for Crowd Machine, a blockchain start-up, reported the theft. As a result, “Harris has been charged with hacking, identity theft, and grand larceny.” As per Dave Berry, one of the REACT investigators: “That’s the long arm of the law.” Mark that as one down for the good guys!
In addition to Harris, there have been other arrests related to the work of the REACT team, one as far away as Florida. Officials claim that many more are in the pipeline, and these arrests are in the U.S. alone. Similar search-and-destroy missions are at work across the globe in the UK, Europe, and India, to name a few. Back in July, Los Angeles police arrested Joel Ortiz, a 20 year-old, at the LAX airport, as he was boarding a plane for Europe. According to the complaint filed, “. Ortiz is now facing 28 charges: 13 counts of identity theft, 13 counts of hacking, and two counts of grand theft.”
Ortiz concocted a clever scheme to attend a convention of crypto investors and then choose his targets wisely: “Ortiz allegedly hijacked around 40 victims’ phone numbers with the help of a gang of scammers. His co-conspirators haven’t yet been named, according to court documents. All together, the crooks allegedly stole $5 million, including some from cryptocurrency investors at a blockchain conference called Consensus that’s run by CoinDesk.”
In the UK, thousands of pounds have been drained from consumer accounts. Local cybercrime research teams have discovered that organized crime gangs are running the scams and may have enabled their fraud by coercing staff in mobile phone shops to bypass necessary fraud checks: “Undercover filming revealed that O2 and Vodafone employees are bypassing basic ID checks and handing over replacement SIM cards to potential criminals.” Since 2016, SIM-Swap scam complaints have skyrocketed by 60%.
How does one protect themselves from SIM-Swap scams?
Due to the nature of this scam, it would be extremely difficult to detect it before it happened. What does happen, once the SIM is swapped, is that your phone literally dies — No messages or calls in or out. If your financial account holders have the capability, request alerts in the form of emails, if and when transfers or major withdrawals take place. Alerts to your phone will not work.
Some banks and phone companies are already attacking the issue from a number of other perspectives, too: “There are multiple organizational and technical ways to combat SIM fraud — from introducing user alerting and additional checks for SIM reissuing to sharing knowledge of SIM swap activity between banks and phone companies. Banks can also consider looking for behavioral changes through behavioral analysis technology that can indicate a compromised device. It is possible to check whether your SIM card number and your international mobile subscriber identity (IMSI) are the same. If there is a discrepancy, your bank could contact you by email or landline to check.”
Concluding Remarks
Just two decades ago, online banking was achieving “critical mass” acceptance by the general public. Smartphones were still an innovation to come, but as with any electronic device today, the criminal element in our society is investing what it takes to find the weak points within these systems. Once compromised, it is only a matter of time before these “weak points” are monetized, typically by draining our financial accounts in an instant. Protect your accounts. Do not load critical access data on your smartphones, but, if you do, maintain a constant vigilance on account balances and transactions.
SIM-Swapping is real and will not be going away soon.
Related Articles
- Forex vs Crypto: What’s Better For Beginner Traders?
- Three Great Technical Analysis Tools for Forex Trading
- What Does Binance Being Kicked Out of Belgium Mean for Crypto Prices?
- Crypto Traders and Coin Prices Face New Challenge as Binance Gives up its FCA Licence
- Interpol Declares Investment Scams “Serious and Imminent Threat”
- Annual UK Fraud Audit Reveals Scam Hot-Spots
Forex vs Crypto: What’s Better For Beginner Traders?
Three Great Technical Analysis Tools for Forex Trading
Safest Forex Brokers 2025
| Broker | Info | Best In | Customer Satisfaction Score | ||
|---|---|---|---|---|---|
| #1 |
|
Global Forex Broker |

BEST SPREADS
Visit broker
|
||
| #2 |
|
Globally regulated broker |

BEST CUSTOMER SUPPORT
Visit broker
|
||
| #3 |
|
Global CFD Provider |

Best Trading App
Visit broker
|
||
| #4 |
|
Global Forex Broker |

Low minimum deposit
Visit broker
|
||
| #5 |
|
Global CFD & FX Broker (*Don’t invest unless you’re prepared to lose all the money you invest. This is a high-risk investment and you should not expect to be protected if something goes wrong. Take 2 mins to learn more) |

ALL-INCLUSIVE TRADING PLATFORM
Visit broker
|
||
| #6 |
|
Global Forex Broker |

Low minimum deposit
Visit broker
|
||
| #7 |
|
CFD and Cryptocurrency Broker |

CFD and Cryptocurrency
Visit broker
|
||
|
|
|||||
Forex Fraud Certified Brokers
Stay up to date with the latest Forex scam alerts
Sign up to receive our up-to-date broker reviews, new fraud warnings and special offers direct to your inbox


